A restaurant kitchen has more to do with computers than you may realize.
(Disclaimer: this essay is an excerpt from my book, Tech Fluent CEO — for “non-technical” founders and professionals who hate calling themselves that. You can get it here for free by paying with a tweet, or purchase it here. Also available on Amazon.)
There’s a huge communication gap between “technical” and “non-technical” people in the industry, even in Silicon Valley.
Non-technical professionals are constantly told that the path to “technical fluency” is through learning to write code or some other kind of intense education. That’s terrible advice. It’s good to give it a try and see if you enjoy it, but it’s mainly useful for people trying to switch careers, not if your goals are different.
Nobody tells you that the “become a pseudo-engineer” route does surprisingly little to improve your technical fluency unless you spend 12+ months on dedicated practice.
That advice is popular to pass around simply because it’s an easy task to teach people how to code. Teaching people to develop technical intuition and systems-thinking is much harder, so nobody does it.
That’s exactly what we’ll be doing in this essay. If you’re an entrepreneur, product manager, executive etc who doesn’t have a software engineering background, read on.
Our goal is that:
- You know exactly how computers work, and why that matters.
- Given a software system — such as the Mars Rover, or Netflix’s site or Doordash’s service, you can visualize and talk about the main functions and components of the system, and the trade-offs involved. You’ll be able to build much better rapport with your technical customers/colleagues.
- If your Uncle Benji came up with an idea for a website/mobile app, or wants to use technology to improve or transform his business, you can translate the idea into a real technical project. You can see if it’s feasible, explain how it would work and figure out rough ballpark cost estimates.
- Given a system, you can understand and imagine all the different ways it could be attacked by hackers.
Let me help you achieve this minimum level of technical fluency.
A moment for my intro:
Hi this is Aman! As an engineer my work has ranged from self-driving trucks, to AI-enabled brain-computer interfaces. I’ve also done enterprise sales, studied film making, and once even sold roses on the street. I like to teach to make hard things simple —simplicity is underrated.
Now sit back, relax, and enjoy the ride.
We’re going to cook a meal.

Foma and Lusha are having dinner tonight. You are the chef responsible for making it happen.
The following high-level things are required for this dinner:
- Ingredients
- Someone to cook the meal
- Space (for storing food, and for cooking)
- A recipe
- Tools, equipment and maybe fuel, for cooking and serving etc
Here’s a quick visual representation:
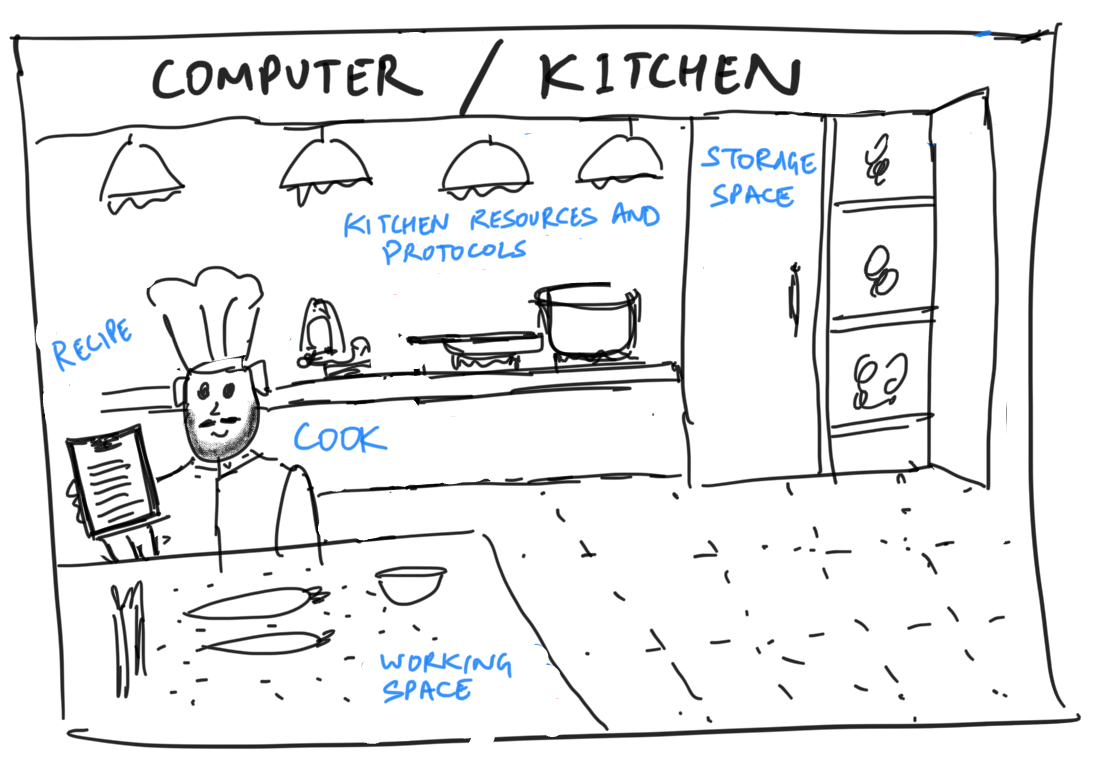
As you can see from the attention to detail in the chef's beard, I am a gifted artist and calligrapher.
None of these things alone would be sufficient, and each one is critical. Here’s the kicker: Every computer system is a kitchen, and all software/computing is essentially a way to achieve these 5 things and tailor them to different kinds of “meals”.
We must start with the basic building blocks of a computer. This cooking analogy will serve you well for almost every software system you imagine in future.
In a computing system, you have information and inputs (or data) that acts as ingredients, and based on that data you have to generate a result which can be consumed by someone else, like a meal.
Every computer has a processor, or a processing unit (CPU), that acts as the cook. This processor works with the ingredients (data). This processor is part of the physical hardware.
The cook also needs space. First, this is where you can store things permanently, like the fridge etc. In your personal computer, this is referred to as disk space—the free space in your hard drive where you store all your files.
Then, there needs to be counter space for cooking. It’s extremely hard to cook a meal if you only have your fridge and a stovetop, and no space to work on! This space in computing is referred to as memory. The RAM (random access memory) is this working space. RAM is not occupied by an item permanently — it can be used for different meals as the need arises, but usually it’s a limited amount of space. If you have a lot of cooks cooking a lot of things at the same time, expanding the working space is very hard even if the storage space is sufficient.
Over the years as technology has developed, processors have become faster and both the storage space and working memory of computers has greatly expanded.

In the 80s, 10 MB of disk space cost >$3,000. Today, you can buy 100,000 times this space for $50.
Now, ingredients can come from the storage, and they can also be new ingredients coming fresh from outside, or even pieces of information that act as commands, eg: Lusha telling you that she is allergic to basil. Or even the order itself, eg: ‘Poutine for my dog please.’ (Just kidding, Canadians I love you.) From a software point of view, all these inputs are just different kinds of data (ingredients).
Finally, there needs to be a recipe for the dish that the processor must execute with the data. This recipe is called software (or “code”, “software program”, “program” etc). We will talk about recipes/software in more detail later.
There are also various appliances and equipment. A kitchen also has some rules and protocols for how things work — and this is especially true for professionally run kitchens. This collection of kitchen rules is the “operating system”, and these things have an impact on what kind of recipes can be executed in a given kitchen.
For example, a kitchen designed only for brewing beer may not be able to handle an order for spicy barbecued pineapple pizza. I’m sorry if you don’t like pineapple pizza because you were not gifted with an elevated sense of taste. Operating systems come in families of varieties like Macintosh, Windows, Linux etc — each is unique in some way.
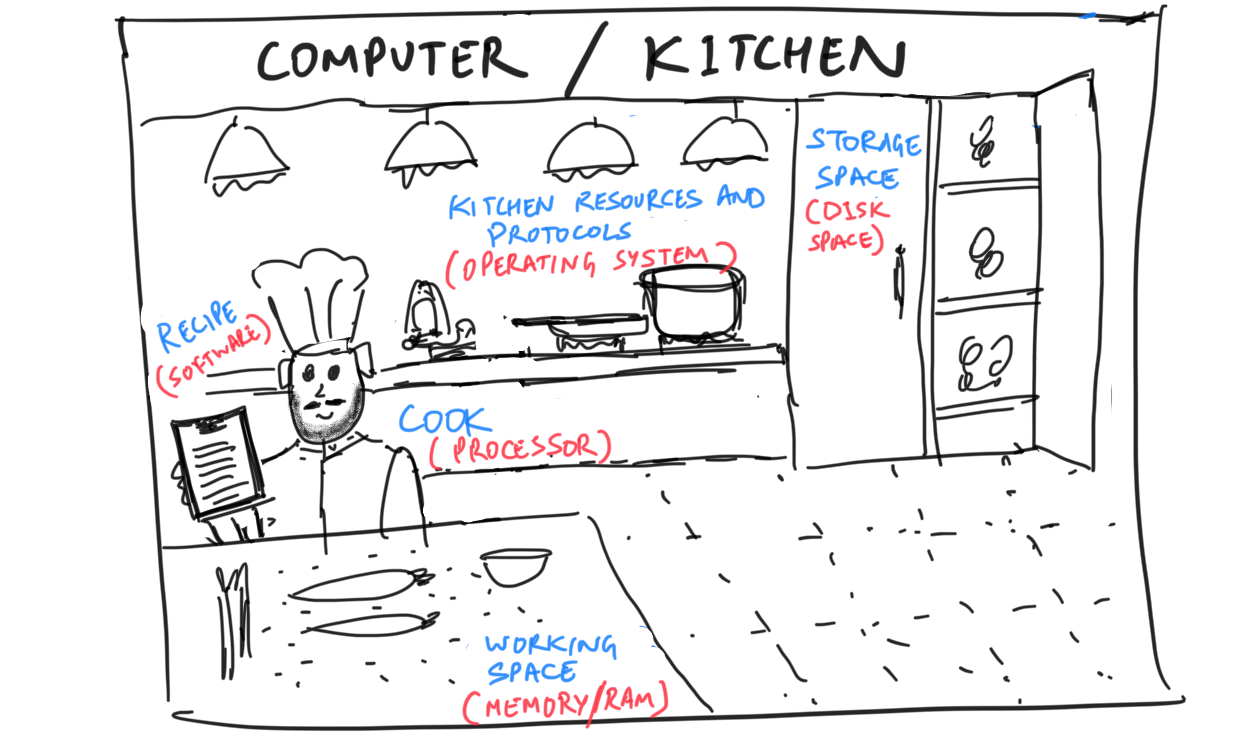
Anyway — as a recap, your computer has a processor that does all the work, it has space of two types: disk space (permanent) and memory/RAM (working space), it has inputs and outputs of data, and it stores computer programs that act as recipes. Depending on the operating system of the computer (tools and rules of the kitchen), some recipes/software can be executed and others cannot.
Did you know that baby penguins sneeze louder than most dogs can bark? Actually this is not true but I had to put a little joke here to force you to take a break.
Software is very much like a food business.

Kitchen at Alinea, a 3 Michelin Star restaurant in Chicago, USA. I'm told they make decent food.
Now that you have at least a fuzzy intuition about computers, we’ll move on to an overview of the modern tech “stack”. Let’s learn about servers, back-ends, front-ends and databases. This is to prepare you for the next section, system design, which is what we’re leading up to.
Before the internet got popular, to use a software application, you had to buy it on a CD or floppy drive and install it on your computer. You were using only your computer’s resources (processors, memory and storage) to do everything. Recall that software applications are recipes followed by the computer hardware. In culinary terms, if you lived on the other side of a big town, you couldn’t get food delivered to your home from a restaurant — you had to buy their recipe and cook it in your own kitchen all by yourself, because delivering it fresh and hot would be impossible.
But what if there was a dedicated motor highway allowing food to be transported to your customer’s home in less than 10 minutes? Wow. Now, if customers just want a good meal of a recipe at their home, they don’t have to cook the thing themselves. (The average home kitchen is not sophisticated enough to cook fancy recipes anyway.) Through food delivery, now the preparation of the food (the back-end) and the plating & eating (the front-end) can be separated by great distances.
Enter the internet! Now that computers can directly connect with each other and share data at great speeds, heavy computation can occur on one computer, and it can send only the results of that computation to another computer. Now, one company (say Google) can invest in massive, powerful computers that crunch millions of web pages every second, and you with your little laptop can benefit from their computation power by only getting the search results served on a platter through your web browser.
Here Google has the back-end of the search application, and the page you see when you open google.com is just the front-end.
The constraint here is internet speed. Faster the internet, the more things can be done over the internet in remote kitchens. Engineers always have to play with this internet speed constraint while designing a system.
A good example is Netflix. While 15–20 years ago it was impractical to play movies online without buffering (for people too young to remember dial-up connections, look up “buffering” :)), today’s laptops don’t even need a slot for DVDs. It’s a testament to how many things can now be delegated to the “back-end”.
Modern devices are quite varied — laptop computers, smart watches, mobile phones, tablets. So a good web service (say Facebook) has to accommodate all these possible clients on the front-end, and be easy to use for everyone.
The buzzword some people use to describe web-based software is the cloud. “Cloud-based applications”, “cloud computing” and what not — it’s just someone else’s computer. It simply means that much of the heavy computation doesn’t happen on your own computer.
The computers on the back-end are called servers. They basically run copies of the same software application, one for each client. These servers often share one huge common storage space, but have a lot of individual RAM (or working memory). The more copies of your software you can create, the more users your product can support at the same time. This is called scaling — just think about how you would ‘scale’ a food business to serve more and more customers.
The data storage (database) is extremely well organized so that servers can retrieve and deposit data to it as efficiently as possible. Depending on the nature of the application, there are different kinds of databases which organize and store data differently. Databases let you easily have consistency of information across distances. This is not trivial. The development of these modern software databases truly changed the world in an unthinkable manner.
Buying something online, reading Wikipedia, social networking, using an ATM— databases are the backbone of our modern digital world.
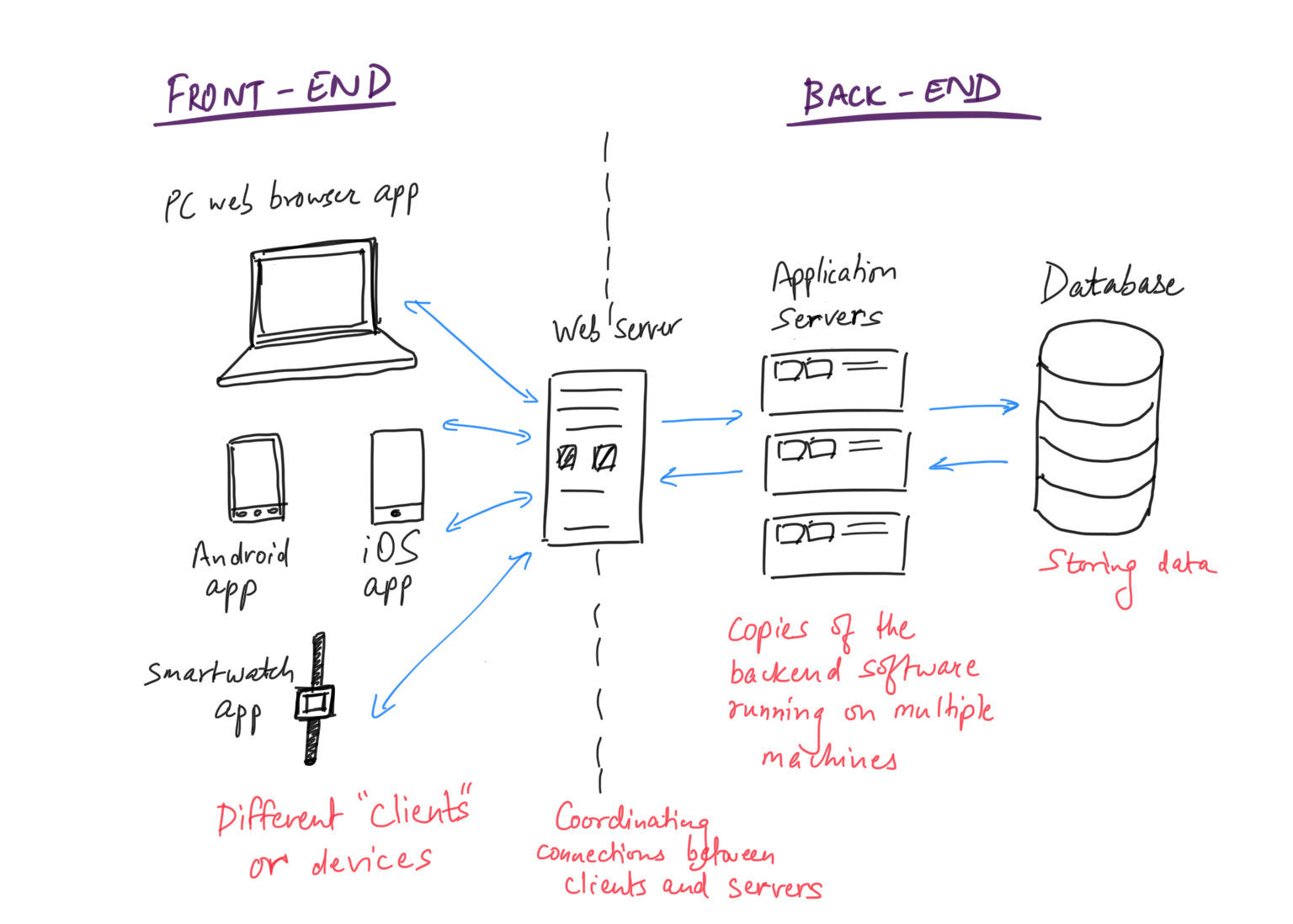
Each individual component of the distributed system/food business performs a unique function, and has different software/code running on it.
If you work closely with engineers, you may hear the word stack. Although the word itself has several meanings, in this context it is just a description of the particular brand or flavor of each of the things that make up the back-end and front-end. Just like you describing your kitchen to a friend. Engineers love having conversations and debates about stacks. It’s akin to a nerdy discussion about kitchen appliances and grocery brands, and some can even get cultish about it.
Consider too that the more things you add to your stack and the more unique it is, the more engineers (and salaries) you need to put into the project.
If you’re interested, here’s an article about Medium’s tech stack. An engineer who can write software programs running across the stack (back-end, front-end, database, etc) is known as a Full Stack Engineer. Such an engineer is capable of building an entire application all by herself. (Though most engineers typically specialize in one area more than the others.)
By the way, talking about innovation, 5G internet is coming quickly. That’s like having warp-speed connections between devices, so the systems you see will likely become even more fragmented and distributed.
Summary: It’s possible and sometimes necessary to separate the different functions of a software system (food business) and create a complex network. Modern communication technology allows these separations to span huge distances — giving birth to the internet.
The internet is essentially a complex network of people cooking, storing, serving and eating each other’s food. It feels like the internet is a “thing”, but it’s just like a large intertwined economy.
Take a 2-minute break if you’re tired.
Now let's exercise our intuition around system design.
(This is the most important part of the essay.)
A food business has to consider things such as the following:
- What’s on the menu
- The target customers and their preferences
- The source of ingredients, their price and quality
- Packaging and delivery mode of the food prepared
- Efficiency and scalability of the kitchen
- Costs of producing the food and delivering it to the customer
Depending on the above 6 factors, your business could vary widely. It could look like a McDonalds franchise, a 3 star Michelin sushi restaurant, Domino’s Pizza, or the company that only makes soy sauce.
Same for software/hardware. Let’s exercise our intuition a little.
- What does the software need to accomplish? Does it control an industrial robot, or a spreadsheet application like Microsoft Excel, or an application like Skype?
- Who are your users and what do they care about? A software that controls a robot surgeon would need to focus on sharp precision and low delay time between calculations, movements and so on, but doesn’t need to have a cute user interface. Therefore, you would ideally want the critical data processing to happen directly on the robot and not on a server elsewhere on the internet, because saving even microseconds of lag time is essential. However, a computer game for 5 year old munchkins would 100% need more effort on the cute user interface than on precision and lag time.
On the other hand, Netflix automatically reduces the video quality when your internet is poor instead of stopping play, because they believe you care slightly more about being able to watch something at all, than about high-definition quality. They designed their system to reflect this belief. - What kinds of services or information does the software need to do its job? Does it need to tell the weather, know about your hotel bookings, the latest stock prices, or your bank balance? And how does your software get that information? Is it available easily on the internet, or do you have to form a digital partnership with all the large banks of the world to get it? (More on this later).
- Packaging and distribution. Your food business could serve ready-to-eat meals on tables and chairs, or deliver the food to be unpacked at home, or even deliver a meal kit that the customer will use to prepare their food.
A service like Netflix can either stream videos over the internet or mail DVDs to homes. A spreadsheet application could be completely offline like Microsoft Excel: 5 years ago when you’d have to download it on your computer. Or like Google Spreadsheets which can simply be accessed online (no download required), or a hybrid of both. - What are the capabilities of the computer on which your software program will run? A Mars Rover cannot connect with the internet directly, but it has wheels, sensors and other apparatus that your software can (and needs to) control. On the other hand, Microsoft Paint can access inputs from a mouse and keyboard, and a video player can use the computer’s screen and speakers.
- Cost — self-explanatory. Economics is often the overriding factor.
A good exercise to practice intuition would be to draw up your own vision of a system you find interesting. Here I’ve made a quick barebones design for an online food delivery company’s system. Start with the customer and go clockwise.
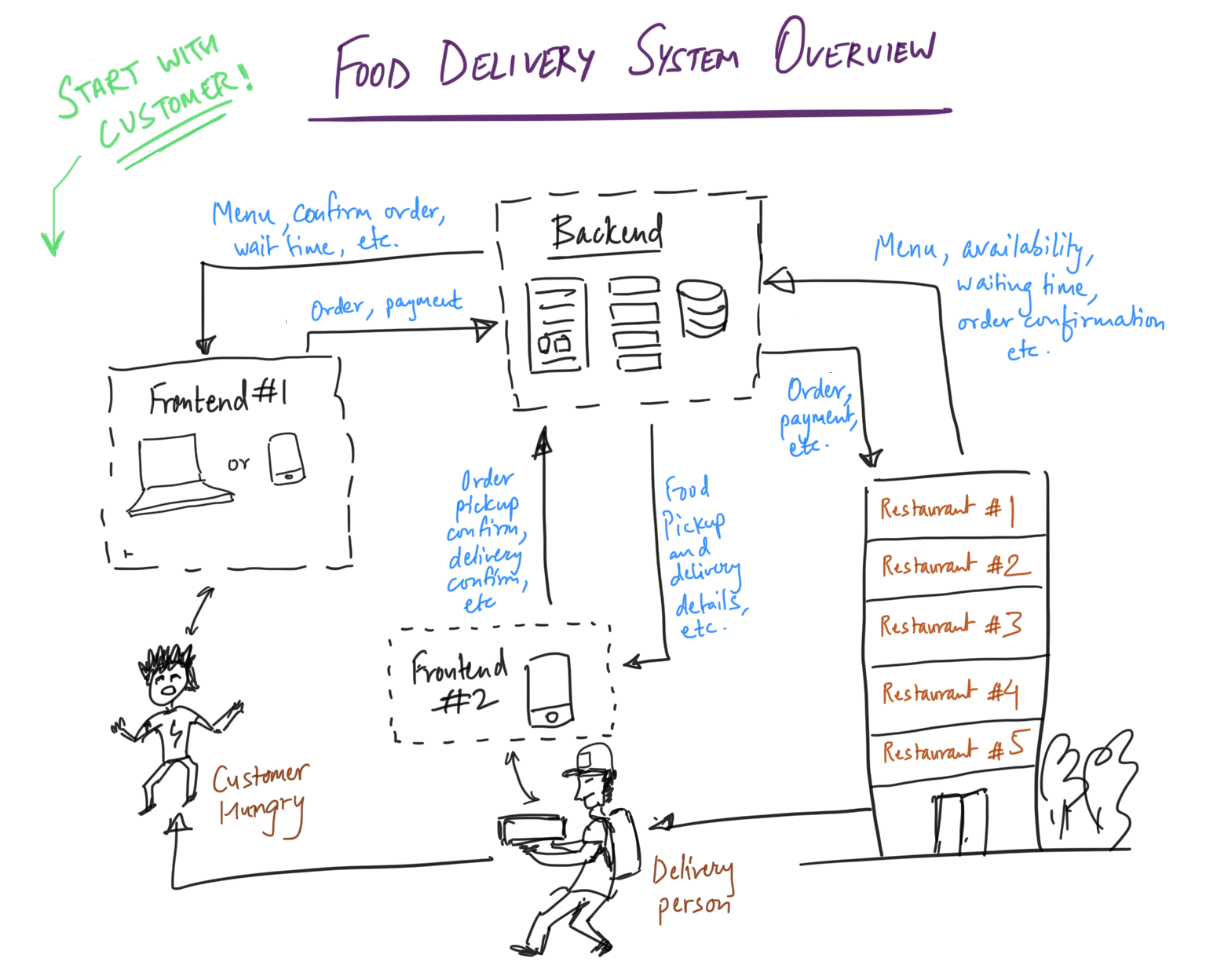
If you want to take a break, I recommend you watch this wonderful 4-minute video about the “Brigade System” used in all luxury restaurants of the world, developed by Auguste Escoffier (1846–1935), a revolutionary French chef who also led the way for many modern cooking methods and ergonomic kitchen plans. He was known as “The King of Chefs, and the Chef of Kings”. As a systems engineer, I applaud the genius of this man.
Cybersecurity Basics

This section will be short and quick. Let’s do a naughty thought experiment.
Say you wanted to do something bad to a food business. Remember that whatever you do, it would cost you time, effort and maybe even money, so you want to profit from this operation if possible.
Naturally the first question is, what should you do? It depends on your goals. Examples:
- Infiltrate the kitchen and spoil ingredients, damage equipment etc.
- Steal their secret recipes.
- Plot with someone to steal money from their cash registers.
- Impersonate a customer and steal the pre-paid food delivery.
- Hire people to crowd the restaurant before peak hour and waste their time, so that their real target customers can’t get service.
- Intercept a food delivery and switch the food with candied chicken.
- Shut down their power abruptly during peak service hours.
It’s also not possible to do anything you want, so usually you’d first need to do a recon mission — go and poke around the restaurant to look for vulnerabilities. For example, when they’re receiving new supplies, is there a small window of time when nobody’s paying attention and you could sneak into the back? Are the locks new or old? Etc etc. The vulnerabilities you find will also dictate what crimes you can pull off.
But you get the idea — any part of the system can be attacked. You can apply the same creativity to software systems. All of the above (and many more) count as valid attacks to a system, and the whole field of cybersecurity is about reducing the risk of each of these. Once again, depending on the nature of your application, some of these attacks are much more damaging than others.
These can be Denial of Service or “DDoS” attack (=crowding the restaurant), Man in the Middle/Eavesdropping, Phishing/Stealing, Malware (=spoiling someone’s kitchen) etc. That’s what people usually mean by “hacking”. It’s not like in the movies where someone takes control of your entire system — that, though theoretically possible, is usually surprisingly hard to pull off even for a simple system, unless the person who built it is a complete dummy.
It’s the same with food safety — people throughout the ages have come up with creative ways to adulterate food for profit, and the world’s food scientists and law enforcement are always in a race against them.
Along the same lines, even if someone’s not trying to hack you, things can go wrong in a food business by mistake. So while developing a system, one should think about other ways the system could fail, define the seriousness of different kinds of failures and figure out a way to increase resiliency against those failures.
The more you separate the parts of a software system and spread them over distances, the more things can individually go wrong and the more things you have to keep track of. But sometimes, keeping things separate can also make them more safe, because then a tiny attack can’t bulldoze through the whole system. There are always trade-offs that engineers work with.
This brings me to another fun fact — computers that controlled US nuclear missiles were, even until 2 years ago, not connected to the internet, and used good old 8-inch floppy disks for sharing information. Fairly un-hackable unless you pulled off a Mission Impossible and physically infiltrated heavily guarded facilities.

The U.S. Military used floppy disks to control nuclear missies until 2018.
I don’t want to go into any more specific details of cyber security — as you can see it is a creative, almost artistic field more than it is technical, and keeps evolving rapidly. What’s important for you is the ability to step back and think like a mischief-maker. It will get better with practice, so keep your naughty hat on at all times. 🙂
Artificial Intelligence
I haven’t covered machine learning and autonomous robots here, but it’s important that you understand them. I have talked about them in another essay.
Wow congratulations, you’ve reached the end of this lesson! Understanding technology always begins with understanding the world you live in — remember that, gentle reader.
As a teacher I like to make a human connection with learners, so I encourage you to leave a comment and share how it helped you, or leave your email below so I can contact you myself! Your stories and feedback give me the energy to keep writing.
Until next time, my friend!